In early November 2019, the Committee on Foreign Investment in the United States (“CFIUS”) initiated a national security review of Beijing Bytedance Technology’s (TikTok’s parent company) acquisition of Musical.ly, a United States social media platform. It is worth noting that this transaction was completed as early as the end of 2017. The media quoted informed sources as having said that “the investigation was mainly focused on data collection.” [1]
Coincidentally, on 18 November 2019, Josh Hawley, a Republican Senator of the United States Congress submitted a bill to the Senate titled the National Security and Personal Data Protection Act of 2019 (“NSPDPA”).[2] The introduction of NSPDPA states that its purpose is “To safeguard data of Americans from foreign governments that pose risks to national security by imposing data security requirements and strengthening review of foreign investments, and for other purposes.”[3]
Although it is uncertain whether and when NSPDPA will pass, the content of NSPDPA has attracted great attention from internet and technology companies around the world. If NSPDPA finally passes, it will create more stringent requirements and challenges for corporate data compliance for Chinese and Russian companies, in particular, and may also apply to countries that are from time-to-time blacklisted by the United States. Therefore, we believe that it is necessary to summarize and comment on United States data protection legislation, in order to prepare for reviews and investigations initiated from time to time by the United States and to provide a reference to China’s legislation on data protection.
Currently, United States data protection legislation is not unified at the federal level and is mostly industry-specific. Thus, we will first briefly introduce data protection acts and bills that have an extraterritorial impact. Then, we will continue to introduce and analyze said acts and bills and their extraterritorial impact.
I. United States acts (or bills) on data protection[4]
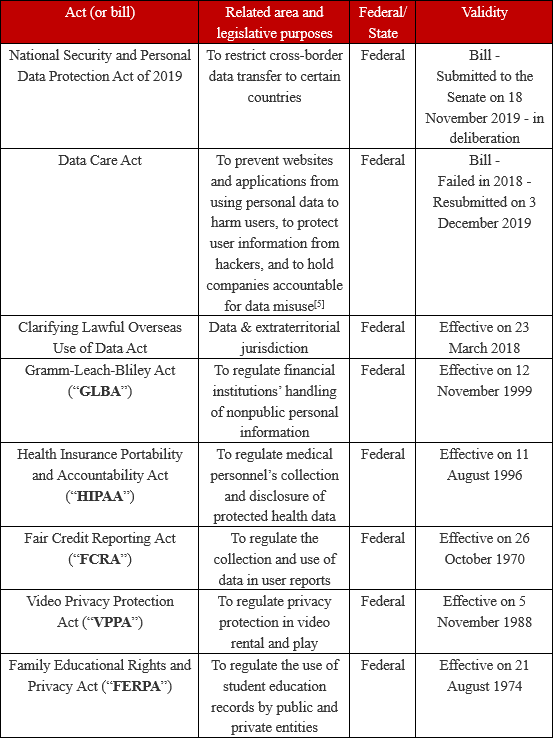
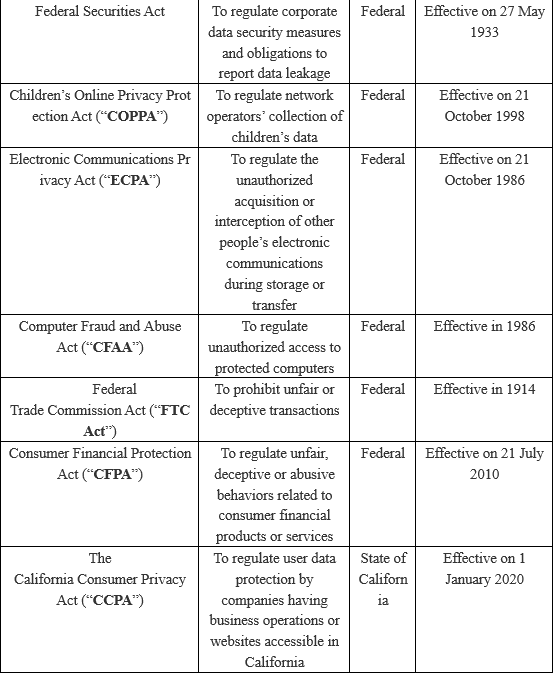
II. National Security and Personal Data Protection Act of 2019 (“NSPDPA”)
Senator Josh Hawley submitted the NSPDPA bill to the Senate Committee on Commerce, Science and Transportation for deliberation on 18 November 2019. The bill is currently supported by Republican senators Tom Cotton and Marco Rubio and is still under deliberation. The NSPDPA bill has six parts, including definitions of the regulated targets, definitions of the data types, special regulations on certain companies’ data collection, special regulations on certain companies’ data storage, penalties for breaches, and approval requirements for specific transactions. The following is a brief introduction of the NSPDPA bill’s regulated targets and related restrictions.
1. The regulated targets of the NSPDPA bill
According to the NSPDPA bill, its legislative purpose is to protect the data of United States citizens and residents against security threats from foreign governments. Therefore, the NSPDPA explicitly aims to do this by targeting certain “Covered Technology Companies” which shall be identified or exempted by the Secretary of State according to relevant procedures once the bill is passed.
In principle, a “covered technology company” is an entity that is established in a Country of Concern, is controlled by a country of concern or a citizen of a country of concern, or is required to submit relevant data to the government of a country of concern. Specifically, a “covered technology company” refers to “an entity that provides an online data-based service such as a website or internet application in or affecting inter-state or foreign commerce”, and it or its parent company is established under the laws of a country of concern; a company or its subsidiaries which is controlled by a citizen or company of a country of concern; or a company that is subject to the jurisdiction of a country of concern so that that country of concern can obtain user data from United States citizens or residents without similar respect for civil liberties and privacy as provided under the Constitution and laws of the United States. Currently, NSPDA only lists two Countries of Concern: China and Russia. Other countries will be identified by the Secretary of State according to certain principles (by considering their laws, policies and practices regarding the protection of data privacy and security) once NSPDA is passed.
2. The special requirements of the NSPDPA bill for “covered technology companies[6]
This part is the core of the NSPDPA bill. It sets a series of special rules for data collection by “covered technology companies”, including:
A. Principle of minimization
User data collected by a “covered technology company” must not exceed the data required for the operation of its website, service or application.
B. Prohibition of secondary use
“Covered technology companies” must not use user data to provide users with targeted advertising, unnecessarily share data with third parties, or unnecessarily promote facial recognition technology.
C. User rights of deletion and access
“Covered technology companies” must allow users to access their data or permanently delete their data in a direct or indirect way.
D. Restrictions on data transfer
All data-based online service companies (including “covered technology companies”) must not directly or indirectly transfer any user data or information required to decrypt the data (such as encryption keys) to any country of concern.
E. Data storage
“Covered technology companies” must not store data or decryption information, such as encryption keys, collected from United States citizens or residents on servers or data storage devices outside the United States.
F. Obligation to report
The management of “covered technology companies” must submit at least one report to the Department of Justice and other relevant departments each year to prove their compliance with NSPDPA.
From the perspective of Chinese companies, the NSPDPA bill mainly has two notable points compared with other data protection acts. Firstly, the NSPDPA bill places clear restrictions on user data transfers from the United States to other countries, especially China. NSPDPA provides a very broad definition of “entities that provide data-based online services.” Therefore, most internet companies will fall under the regulation of NSPDPA. If the NSPDPA bill passes, most Chinese internet companies, such as those whose business involves collecting user data from the United States, might need to set up oversea entities, “localize” data, and establish data isolation mechanisms so as to meet compliance requirements. Secondly, the NSPDPA bill defines and restricts targeted advertising and facial recognition technologies that are based on user information and online search habits. These two technologies are now widely used in practice. Targeted advertising based on user information and online search habits is already a very mature business model. Facial recognition technology is currently the focus of many internet companies for future development. Now it is mainly used for identity verification and has been widely applied to banking and payment services. If the NSPDPA bill passes, relevant companies will need to differentiate their business strategies based on data sources and develop systems that comply with the laws of the United States.
III.Clarifying Lawful Overseas Use of Data Act (“CLOUD Act”)[7]
Before introducing this act, we would like to highlight a problem that exists because of existing laws. In early 2018, Apple transferred iCloud services for users in Mainland China to Yunshang Aipo (Guizhou) Technology Co., Ltd., (“Cloud Guizhou”). When users start the iCloud service, their personal data (such as contacts, calendar, photos, notes, reminders, files, application data, and iCloud emails) are automatically sent to and stored by Cloud Guizhou.[8] So, if the United States Government requires Apple to provide it with the iCloud data of users in Mainland China, should Apple cooperate and can Apple refuse to do so by arguing that it is against Chinese law?
In fact, one of the main purposes of the CLOUD Act was to solve the above problem. At that time of its enactment, there was a controversial dispute between the United States Government and Microsoft over extraterritorial data collection. In 2013, while investigating a drug trafficking case, the Southern District Court of the State of New York issued a search warrant ordering Microsoft to provide all emails and information relating to a particular user. That user’s information was stored on a server in the United States, but his emails were stored on a server in Ireland. Microsoft filed a lawsuit with the Southern District Court of the State of New York to challenge the validity of the said search warrant, on the grounds that the United States Government has no right to require United States companies to provide data stored outside the United States.[9]This case went through the Federal District Court and the Court of Appeal all the way to the Supreme Court. When this case was being heard by the Supreme Court, the CLOUD Act was assented to by the President and entered into force. The CLOUD Act §103(a)(1) states that: “A [service provider] shall comply with the obligations of this chapter to preserve, backup, or disclose the contents of a wire or electronic communication and any record or other information pertaining to a customer or subscriber within such provider’s possession, custody, or control, regardless of whether such communication, record, or other information is located within or outside of the United States.”[10] As a result, the Supreme Court ruled that no live dispute remained between the parties because Microsoft was obliged to disclose the relevant data, and so, they rejected Microsoft’s claims.
The CLOUD Act had been jointly proposed by four Republican and Democratic senators in February 2018. It was quickly assented to by President Trump and became effective on 23 March 2018. The CLOUD Act is an abbreviation for the Clarifying Lawful Overseas Use of Data Act, which is an amendment to the United States Electronic Communications Privacy Act of 1986. According to The Purpose and Impact of the CLOUD Act[11] issued by the U.S. Department of Justice, the core purpose of the CLOUD Act is to further optimize the procedures for foreign governments and the United States Government to collect important data information through network service providers in order to deal with the increasing terrorism, violent crime, and cybercrime.
In the following, the relevant provisions of the CLOUD Act are briefly introduced.
1. Provisions regarding the United States Government’s collection of data stored in foreign countries through network service providers
According to the CLOUD Act, United States network service providers shall disclose the data they control to the United States Government by default, and they can only file a motion against the required disclosure when certain conditions are met. The courts will consider various factors in granting such motions.
A. Preservation and disclosure of communication records
Regardless of whether the communication content, records or other information stored by a network service provider is located in the United States, so long as the network service provider owns, controls or regulates the above content, records or information, it is required by the CLOUD Act to preserve, backup, and disclose such information.
B. Motions to quash or modify the legal process
If a network service provider reasonably believes that: 1) the customer or subscriber is not a United States person and does not reside in the United States; and 2) the required disclosure would create a material risk that the provider would violate the laws of a Qualifying Foreign Government, it can file a motion to modify or quash the legal process which requests it to disclose information.
C. Factors for the court to grant a motion
After the network service provider files a motion, the court also needs to consider factors relating to the “overall situation.” There are eight factors, which mainly consider the interests of the United States, the losses that foreign governments may suffer due to disclosure, the difficulties caused by the required disclosure to network service providers, the citizenship of target users and their relevance to the United States and foreign governments, and whether negative effects that can be avoided by other means of disclosure.
2. Provisions regarding foreign governments’ collection of data stored in the United States through network service providers
If a foreign government wants to collect data stored in the United States, its country must firstly be a “qualifying foreign government” as defined by the CLOUD Act, and secondly meet other specific restrictions.
A. “Qualifying Foreign Government”
According to the CLOUD Act, only “qualifying foreign governments” can apply to access data located in the United States through network service providers. The “qualifying foreign governments” identified by the CLOUD Act must firstly sign a bilateral agreement with the United States. Moreover, qualifying countries should have substantive and procedural laws on privacy and civil liberties. The assessment of whether there are corresponding laws should be considered from two points: firstly, whether the country is a party to the Cyber Crime Convention (there are currently 64 parties to the Cyber Crime Convention, and China is not one of them[12]). Secondly, whether the country’s domestic laws have provisions consistent with Chapters 1 and 2 of the Cyber Crime Convention[13]. In addition, it is also necessary to consider whether the country respects laws, non-discrimination principles, and human rights, whether it has adequate data protection mechanisms, and whether it promotes the free flow of information worldwide and the opening of the internet.
B. Limitations to data collection by a “qualifying foreign government”
A “qualifying foreign government” does not automatically have the right to collect data. The CLOUD Act provides various limitations on data collection by foreign governments. The United States Government will cooperate with data collection by foreign governments only when all of its requirements are met. The specific requirements are:
1) the foreign government may not intentionally target a United States person or a person located in the United States, and shall adopt targeting procedures designed to meet this requirement; 2) the foreign government may not target a non-United States person located outside the United States if the purpose is to obtain information concerning a United States person or a person located in the United States; 3) the foreign government may not issue an order at the request of or to obtain information to provide to the United States Government or a third-party government, nor shall the foreign government be required to share any information produced with the United States Government or a third-party government; 4) an order issued by the foreign government -
a. shall be for the purpose of obtaining information relating to the prevention, detection, investigation, or prosecution of serious crime, including terrorism;
b. shall identify a specific person, account, address, or personal device, or any other specific identifier as the object of the order;
c. shall be in compliance with the domestic law of that country;
d. shall be based on requirements for a reasonable justification based on facts, particularity, legality, and severity regarding the conduct under investigation;
e. shall be subject to review or oversight by a court, judge, magistrate, or other independent authority; and
f. in the case of an order for the interception of communications shall require that the interception order be for a fixed, limited duration and be issued only if the same information could not reasonably be obtained by another less intrusive method;
5) an order issued by the foreign government may not be used to infringe freedom of speech; 6) the foreign government shall promptly review material collected pursuant to the agreement and store any unreviewed communications on a secure system; 7) the foreign government shall take measures to isolate the obtained communications unless they are related to serious crime; 8) the foreign government may not disseminate the content of a communication of a United States person to United States authorities unless the communication relates to serious crime; 9) the foreign government shall afford reciprocal rights of data access; 10) the foreign government shall agree to periodic review of compliance by the foreign government with the terms of the agreement to be conducted by the United States Government; and 11) the United States Government shall reserve the right to render the agreement inapplicable as to any order of foreign governments.
It can be seen from the background of the CLOUD Act that its main purpose is to solve the problem of the government intercepting data from the data owner. This problem has a long history in the United States. Administrative agencies generally obtain data by applying for subpoenas, and private companies are often reluctant to provide data for reasons of protecting personal privacy and maintaining their company reputation. To a certain extent, the CLOUD Act can help to resolve the network service provider’s dilemma of having to choose between law enforcement agencies and users.
Returning to the problem about iCloud, it is not difficult to see that since China is not a “qualifying foreign government” as defined by the CLOUD Act, and Apple has control over the data stored in Cloud Guizhou, if the United States Government requests Apple to provide the iCloud data stored in Cloud Guizhou, Apple may not be eligible to file a motion to prevent this.
In summary, although the NSPDPA bill is currently only in the initial stages of the legislative process, has yet to be passed by both the Senate and the House of Representatives, and assented to by the President, it will profoundly impact cross-border data transfers once it enters into effect. Therefore, it is necessary for relevant companies to adjust their business strategies and to establish relevant compliance mechanisms in advance, so as to avoid possible adverse effects on their business. The CLOUD Act specifies that the government needs to abide by certain rules when intercepting user data. It mainly relates to cross-border data transfers initiated by the United States Government and other qualifying foreign governments. Chinese companies should understand the content of the CLOUD Act so that they can prepare for data collection requests from the United States Government.
The above-mentioned acts are available at:
Clarifying Lawful Overseas Use of Data Act (“CLOUD Act”)
http://www.lifanglaw.com/uploads/tmp/CLOUD.pdf
National Security and Personal National Security and Personal Data Protection Act of 2019 (“NSPDPA”)
http://www.lifanglaw.com/uploads/tmp/NSPDPA.pdf
[1] https://www.reuters.com/article/us-tiktok-cfius-exclusive/exclusive-us-opens-national-security-investigation-into-tiktok-sources-idUSKBN1XB4IL
[2] https://www.congress.gov/bill/116th-congress/senate-bill/2889/text?r=1&s=2
[3] “To safeguard data of Americans from foreign governments that pose risks to national security by imposing data security requirements and strengthening review of foreign investments, and for other purposes ”
[4] https://fas.org/sgp/crs/misc/IF11207.pdf
[5] https://www.schatz.senate.gov/press-releases/schatz-leads-group-of-16-senators-in-reintroducing-legislation-to-help-protect-peoples-personal-data-online
[6] NSPDPA SEC. 3. DATA SECURITY REQUIREMENTS FOR COVERED TECHNOLOGY COMPANIES.
[7] https://www.justice.gov/dag/page/file/1152896/download
[8] https://www.apple.com/legal/internet-services/icloud/cn_si/gcbd-terms.html
[9] https://en.wikipedia.org/wiki/Microsoft_Corp._v._United_States
[10] https://www.supremecourt.gov/opinions/17pdf/17-2_1824.pdf
[11] https://www.justice.gov/dag/page/file/1153436/download
[12] https://www.coe.int/en/web/conventions/full-list/-/conventions/treaty/185/signatures?p_auth=6BTyfyHl
[13] Chapter I – Use of terms(Article 1 – Definitions);Chapter II – Measures to be taken at the national leve l(Article 2 – Illegal access; Article 3 – Illegal interception; Article 4 – Data interference; Article 5 – System interference; Article 6 – Misuse of devices; Article 7 – Computer-related forgery; Article 8 – Computer-related fraud; Article 9 – Offences related to child pornography; Article 10 – Offences related to infringements of copyright and related rights; Article 11 – Attempt and aiding or abetting; Article 12 – Corporate liability; Article 13 – Sanctions and measures; Article 14 – Scope of procedural provisions; Article 15 – Conditions and safeguards; Article 16 – Expedited preservation of stored computer data; Article 17 – Expedited preservation and partial disclosure of traffic data; Article 18 – Production order; Article 19 – Search and seizure of stored computer data; Article 20 – Real-time collection of traffic data; Article 21 – Interception of content data; Article 22 – Jurisdiction)
Practices



