On March 22, 2024, the Cyberspace Administration of China (“CAC”) officially released the Provisions on Promoting and Regulating Cross-Border Data Flows (the “Provisions”)[1], optimizing and adjusting cross-border data transfer systems such as security assessment of cross-border data transfer, standard contract for cross-border transfer of personal information and personal information protection certification. On the same day, the CAC also issued the updated versions of the Guidelines on Application for Security Assessment of Cross-Border Data Transfer (Second Edition) and the Guidelines on Filing of the Standard Contract for Cross-Border Transfer of Personal Information[2], which simplify the proceedings, methodologies and materials for application for security assessment and filing of standard contract and are in line with the overall optimization of the cross-border data transfer system. Regarding the newly issued data transfer regulations, we briefly summarized the key takeaways of the Provisions for future reference of enterprises in their subsequent compliance reviews and improvements involving cross-border data flows.
Key Takeaways of the Provisions
1. Exemptions from Cross-Border Data Transfer System
Generally, to ensure the compliant cross-border data transfer, enterprises should comply with the existing cross-border data transfer systems, and choose to apply for security assessment of cross-border data transfer, enter into standard contract for cross-border transfer of personal information or obtain personal information protection certification based on factors such as category, quantity and scenario of the transferred data. These are the three traditional regulatory approaches for cross-border data transfer.
The Provisions specifies different exemptions from cross-border data transfer system.
• Data collected and generated in international trade, cross-border transportation, academic cooperation, multinational manufacturing and marketing activities that do not contain personal information or important data can be exempted from the three traditional regulatory approaches.
This exemption facilitates trade activities and academic exchanges between domestic and foreign enterprises/institutions. However, domestic enterprises/institutions still need to note that the important data directories or guidelines of specific industries or regions may classify data with outbound volume reaching a certain threshold as important data, rendering the exemption scenario inapplicable in such cases.
• Data that is collected and generated from abroad, transmitted to China for processing and then re-transferred abroad without introducing domestic personal information or important data during the procedure can be exempted from the three traditional regulatory approaches.
This provision substantially mitigates the compliance burden for domestic enterprises providing overseas-oriented data cloud services. At the same time, it will attract various enterprises to conduct offshore data processing business in China as an “offshore data center” with both ends located overseas, facilitating further development of China’s data transactions.
• Providing personal information (excluding important data) abroad which meets one of the following conditions (see table below) can be exempted from the three traditional regulatory approaches. Among them, conditions 1-3 cover common international trade scenario, international human resource management scenario, and emergency scenario, effectively reducing the transaction and management costs for multinational enterprises.
• 1: [Performance of Individual Contract] When it is necessary to provide personal information abroad for the purpose of entering into or performing a contract in which the individual is one of the parties. |
• 2: [Human Resource Management] When it is necessary to provide employee personal information abroad for the cross-border human resource management based on labor rules and regulations formulated pursuant to laws and collective contract signed pursuant to laws. |
• 3: [Emergency Exemption] When it is necessary to provide personal information abroad for the protection of individual’s life, health, and property safety under emergencies. |
• 4: [Below Cumulative Threshold] Data processor who is not a Critical Information Infrastructure Operator has cumulatively provided non-sensitive personal information of less than 100,000 individuals abroad since January 1 of the current year. |
It is worth noting that when tracing back to the exemption for human resource management in the exposure draft of the Provisions, it was stipulated that “personal information of internal employees must be provided abroad for human resource management based on labor rules and regulations formulated pursuant to laws and collective contract signed pursuant to laws.” However, in the final version of the Provisions, it is revised to “when it is necessary to provide employee personal information abroad”. The word “must” is changed to “necessary”. We tend to believe that it shows the cyberspace administration department’s attitude to relatively loosening the restrictions on multinational enterprises transferring employee personal information across borders based on the department’s experience in reviewing previous security assessment applications and standard contract filings.
How to identify important data?
Regarding the definition of “Important Data”, the Data Security Law stipulates that various regions and departments shall determine the specific important data directories within their respective regions/departments/industry sectors in accordance with the category-based and class-based data protection system and shall provide focused protection for the data listed in the directories. Enterprises can refer to the Appendix G Guidelines for Identifying Important Data in the newly released Data Security Technology — Rules for Data Classification and Grading (GB/T 43697-2024)[3] as well as directories published by relevant regional departments. On the one hand, Article 2 of the Provisions clearly states that important data will be notified or publicly released by relevant departments and regions. If data has not been publicly identified as important data, enterprises are not required to submit it for application for security assessment of cross-border data transfer. Meanwhile, enterprises still need to classify and categorize their own business data based on the directories published by relevant departments and the Data Security Technology — Rules for Data Classification and Grading to identify whether they may fall within the scope of relevant important data directories and to fulfill corresponding compliance obligations.
2. Regulatory Approaches for Cross-Border Data Transfer of CIIOs and Non-CIIOs
The Provisions categorizes data processors into two major groups: Critical Information Infrastructure Operators (“CIIOs”) and other data processors that are not CIIOs. Articles 7 and 8 of the Provisions outline three regulatory approaches that are applicable to data processors, including applying for security assessment of cross-border data transfer, entering standard contract for cross-border transfer of personal information or obtaining personal information protection certification, as well as applying exemptions/special provisions.
(1) Regulatory approaches for cross-border data transfer of CIIOs
According to the Regulations on Security Protection of Critical Information Infrastructure, critical information infrastructure refers to important network facilities and information systems and others that, if destroyed, malfunction, or suffer data breaches, would seriously endanger national security, national economy and people’s livelihood and public interests. These often involve key industries and sectors such as public communication and information services, energy, transportation, water conservancy and finance. Enterprises do not need to assess whether they are CIIOs on their own. The authorities in relevant industries and sectors will notify the results to the determined CIIOs. If an enterprise is not notified, it can be considered as a Non-CIIO.
| Applying for security assessment of cross-border data transfer to national cyberspace administrations | When CIIOs provide personal information or important data abroad |
| Exemptions or applying special systems of FTZ | When comply with the aforementioned exemption scenarios or the Free Trade Zone (“FTZ”) negative list system (Articles 3, 4, 5 and 6 of the Provisions) |
It can be seen that, generally, CIIOs are required to burden heavier compliance obligations for cross-border data transfer when providing personal information or important data abroad. However, specific scenario factors can override the type of data processor, and in cases where exemptions apply, CIIOs may be exempted from applying for security assessment of cross-border data transfer.
(2) Cross-border data transfer regulation of Non-CIIOs
The regulation of cross-border data transfer of other data processors that are not CIIOs is relatively relaxed and can be divided into three categories according to the type of the transferred data and the cumulative amount of information since January 1 of the current year.
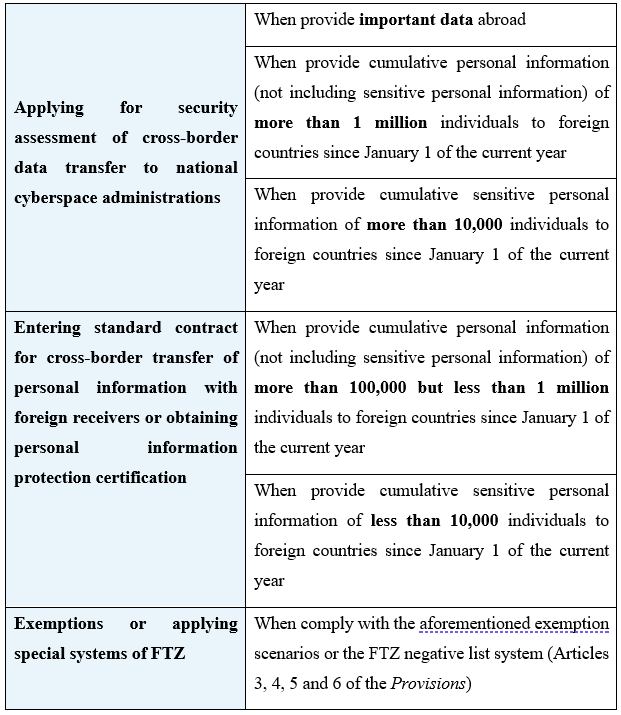
How to cumulatively calculate the personal information volume?
First, it is clear that the above cross-border data transfer volume threshold is the result of counting after deduplication in terms of natural persons. For example, if a domestic subsidiary of a multinational enterprise transfers the personal information of Employee A in the employee on-boarding data management scenario, and also transfers the personal information of Employee A in the welfare application scenario, the number of individuals shall be counted as one after deduplicating in different scenarios.
Secondly, the cumulative number of individuals counted should remove the cases that fall under the first three subparagraphs of Article 5 of the Provisions. It is worth discussing whether the cross-border transfer of sensitive personal information is also included in the aforementioned exemptions, i.e., if the Provisions specifies a threshold of sensitive personal information of 10,000 individuals, should the 10,000 individuals remove the number of people whose sensitive personal information being provided abroad for “performance of individual contract”, “human resource management”, and “emergency situations”, as referred to in Article 5 of the Provisions? Based on the fact that Article 5, subparagraphs 1-3 of the Provisions do not stipulate “(not including sensitive personal information)” in the personal information in the exemption scenarios, and in light of the reply[4] given by the CAC to the reporters’ questions on the Provisions, we understand that if an enterprise transfers both general personal information and sensitive personal information abroad under the exemption scenarios, the number of individuals pertaining to sensitive personal information should not be counted in the cumulative number of 10,000 individuals.
3. Reserving Space for Exploring the Negative List System in FTZs
Article 6 of the Provisions stipulates that the Pilot FTZs may explore to implement the negative list system, and that data processors (regardless of whether they are CIIOs or not) in FTZs may be exempted from the application of the three traditional regulatory approaches for cross-border data transfer in case that they provide data abroad which are not included in the negative list. However, if the FTZ negative list is not in place, data processors in the FTZ should still execute their cross-border data transfer activities in accordance with the relevant provisions of the national security management of cross-border data transfer.
For FTZs, if a FTZ is to formulate the data negative list within the zone, the relevant list shall follow the framework of the national category-based and class-based data protection system, seek for approval of the provincial-level cyberspace affairs commission, and report to the national cyberspace administration department and the national data management department for the record.
Enterprises can pay more attention to the corresponding list directories and standard contract guidelines and other regulations and policy documents issued by different FTZs. Different FTZs (Shanghai, Beijing, Tianjin and other FTZs) and specific regions (such as the Guangdong-Hong Kong-Macao Greater Bay Area, etc.) will have different policy preferences and regulations on industry sectors, data categories and cumulative volumes, etc. Enterprises should continue to pay attention to the favorable data flow regulatory developments that may be released therein.
4. Other Key Takeaways of the Provisions
Apart from the above key articles that require special attention, the Provisions also explicitly stipulates other takeaways of regulation of cross-border data transfer.
• Article 9 of the Provisions adjusts the validity period of security assessment results of cross-border data transfer to three years. For enterprises which need to continue to carry out cross-border data transfer activities and are unnecessary to re-apply for the assessment, a new system has been added for applying for an extension of the validity period of the assessment, whereby the data processor may apply for an extension within 60 days before the expiry of the validity period. The assessment results may be valid for another three years upon approval by the national cyberspace administration department.
• Articles 10 and 11 of the Provisions also remind data processors of their other data compliance obligations. In addition to cross-border data transfer compliance obligations, data processors are also required to fulfill obligations such as obtaining the individual’s separate consent, protection of personal information and data security.
Enterprise Compliance Tips
1. Tone of the Provisions: Promoting Transactions and Refining Full-Chain Regulation
Preliminarily, the Provisions has released positive signals to promote data flows and cross-border transactions, and the supporting Guidelines for the Application for Security Assessment of Cross-Border Data Transfer (Second Edition) and Guidelines for Filing for Standard Contracts for Cross-Border Transfer of Personal Information (Second Edition) documents updated on the same day have simplified the procedural process compared with the initial version, which essentially help enterprises to reduce the cost of compliance and increase the transparency of fulfillment of data compliance obligations.
Meanwhile, the reduction of procedural compliance burden for enterprises does not mean the relaxation of substantive regulation of cross-border data transfer compliance. Article 12 of the Provisions emphasizes that local cyberspace administration departments should strengthen the full-chain, full-domain regulation before, during and after the event, and that the regulatory philosophy has shifted from emphasizing prior regulation to the full-chain regulation, which actually strengthens substantive requirements for enterprises to fulfill their data compliance obligations throughout the entire business process.
2. Compliance Transition Strategies for the Integration of New and Old Systems
Based on their specific situations regarding cross-border data transfer compliance, enterprises can refer to the Provisions and relevant policy interpretations to select suitable transition strategies.
Enterprises that have already passed the security assessment of cross-border data transfer may continue with their cross-border data transfer activities.
Enterprises that have not yet passed the security assessment of cross-border data transfer but may be exempted from the assessment according to the Provisions can instead transfer the data abroad through other methods such as signing standard contracts for cross-border data transfer of personal information or obtaining personal information protection certification.
Enterprises that have already applied for security assessment for cross-border data transfer or filed for standard contracts for cross-border data transfer of personal information, but according to the Provisions do not need to undergo the above procedures, can proceed data according to the original procedures, or, withdraw their applications or filings to the local provincial-level cyberspace administration department.
3. Maintain Regular Records of Information Volume and Strengthen Internal Compliance Documentation
Considering that the Provisions stipulates that the statistical period for cumulative data volume is from January 1 of the current year to the date of the security assessment of cross-border data transfer and requires to remove the data quantities under the exemption scenarios and the duplicated data, there is a certain requirement for the precision of outbound data quantity statistics. Especially for enterprises with perennial business needs for cross-border data transfer, it would be most advisable to establish a routine data recording system to comply with administrative verification requirements.
The refined full-chain regulation of cross-border data transfer under the Provisions means that enterprises cannot only count on certain “hasty compliance” before the data transmission. Instead, they need to comprehensively consider all data compliance obligations throughout the entire cross-border information transfer process and maintain corresponding documents or activity proof records. This will enable enterprises to promptly provide relevant compliance proof when the regulatory authorities conduct post-event regulation/assessment or when policies are adjusted.
Reference
[1] https://www.cac.gov.cn/2024-03/22/c_1712776612187994.htm
[2] https://www.cac.gov.cn/2024-03/22/c_1712783131692707.htm
[3] https://www.tc260.org.cn/upload/2024-03-21/1711023239820042113.pdf
[4] https://mp.weixin.qq.com/s/-Y-dY_HL21jHTFQsMbeiVQ?scene=21#wechat_redirect
Professionals
Practices



